OpenBGPD Looking Glass
BGP Looking Glass with OpenBSD
something I’ve wanted to do for a long time and never got around to it …
Just give a try, it’s public available: https://bgp.stoege.net/
Prerequisite
- OpenBSD VM (at least 2G RAM)
- Public IPv4 / IPv6
- DNS Record / Static IP
- Full BGP Feed (don’t worry, you can get it for free)
httpd config
OpenBSD got their own HTTP Daemon in Base System. Let’s enable and configure it.
export fqdn="bgp.example.com"
or
export fqdn=$(hostname); echo $fqdn
httpd.conf
cat << EOF > /etc/httpd.conf
# httpd.conf
types {
include "/usr/share/misc/mime.types"
}
# http server -> redirect
server "$fqdn" {
listen on * port 80
log access "nossl-${fqdn}.log"
location "/.well-known/acme-challenge/*" {
root "/acme"
request strip 2
}
location * {
block return 302 "https://${fqdn}"
}
}
# https server
server "${fqdn}" {
listen on * tls port 443
log access "${fqdn}.log"
tls {
certificate "/etc/ssl/${fqdn}.fullchain.pem"
key "/etc/ssl/private/${fqdn}.key"
}
location "/cgi-bin/*" {
fastcgi socket "/run/slowcgi.sock"
root ""
}
location "/" {
block return 302 "https://${fqdn}/cgi-bin/bgplg"
}
}
EOF
enable and start services
rcctl enable httpd slowcgi
rcctl start httpd slowcgi
acme config
we wanna use tls …
cat << EOF > /etc/acme-client.conf
# acme-client.conf
authority letsencrypt {
api url "https://acme-v02.api.letsencrypt.org/directory"
account key "/etc/acme/letsencrypt-privkey.pem"
}
authority letsencrypt-staging {
api url "https://acme-staging-v02.api.letsencrypt.org/directory"
account key "/etc/acme/letsencrypt-staging-privkey.pem"
}
#
# My Stuff
#
domain $fqdn {
domain key "/etc/ssl/private/${fqdn}.key"
domain full chain certificate "/etc/ssl/${fqdn}.fullchain.pem"
sign with letsencrypt
}
EOF
set permission
chmod 600 /etc/acme-client.conf
chown root:wheel /etc/acme-client.conf
allow on pf.conf
be aware that your firewall needs to allow http from any for tls cert setup. put something like this after your default deny rule. if you’re not comfortable with the packet filter on openbsd, i highly recommend this few slides from Peter Hansteen, Massimiliano Stucchi, Tom Smyth / BSDCAN 2022.
block all
---
pass in log quick proto tcp from any to (self) port { 80 443 }
---
get tls cert
acme-client -v ${fqdn}
renew cert automatically
add the following line to your crontab
~ ~ 1 * * -ns acme-client your.fqdn.dot.com && rcctl reload httpd
BGP Full Feed for free
the most critical part may be the BGP Fulltable. If you’re a network engineer, you may have access to some routers where you can peer with. for lab and experimental usage, you can peer with AS 57355 / Lukasz Bromirski -> RPKI for Home Usage.
bgpd.conf
replace the router-id with your public ip (for example). it must be unique, your public ip should be find
export pubip="your-public-ip-address"
or get your public ip automatically if you have the ‘i3’ script installed from ip.inno.ch
export pubip=$(i3 -b -4)
deploy the bgpd.conf
cat << EOF > /etc/bgpd.conf
# define our own ASN as a macro
ASN="65001"
# global configuration
AS \$ASN
router-id $pubip
# this line is important !
nexthop qualify via default
# BGPLG
socket "/var/www/run/bgpd.rsock" restricted
# No need to update the fib for looking glass
fib-update no
# hold time
holdtime 7200
# validate rpki
include "/var/db/rpki-client/openbgpd"
neighbor 85.232.240.179 {
remote-as 57355
descr "lukasz.bromirski.net-4"
multihop 15
}
neighbor 2001:1A68:2C:2::179 {
remote-as 57355
descr "lukasz.bromirski.net-6"
multihop 15
}
## rules section
allow quick from ebgp
deny quick to ebgp
EOF
set permission
chmod 600 /etc/bgpd.conf
chown root:wheel /etc/bgpd.conf
and start the bgpd daemon
rcctl enable bgpd
rcctl start bgpd
now, you should get a BGP Fullfeed like this:
# bgpctl show sum
Neighbor AS MsgRcvd MsgSent OutQ Up/Down State/PrfRcvd
lukasz.bromirski.net-4 57355 251013 36 0 22:50:34 880585
lukasz.bromirski.net-6 57355 129939 36 0 22:50:34 148767
enable rpki
The OpenBSD Guys wrote a own RPKI Client and included them in the Base System. We just have to enable the regulary Update in the Crontab
update every hour
# Update rpki client every hour
~ * * * * -ns nice rpki-client -v && bgpctl reload
BGP Looking Glas
all the files for BGP Looking Glass are already installed. You just need to set Permission / Ownership and you’re done
chmod 0550 /var/www/cgi-bin/bgplg
chown www:daemon /var/www/cgi-bin/bgplg
chmod 0555 /var/www/bin/bgpctl
chmod 4555 /var/www/bin/ping* /var/www/bin/traceroute*
Mount /var without nosuid
the http daemon is running in a chrooted environment for security reason. as we now have some binaries in the /var/www partition, we have to remount the /var partition without the nosuid flag. otherwise, the few binaries (ping, traceroute) are not allowed to run from this location with suid rights.
mount -u -o suid /var
and make it reboot safe
sed -E -i.bak 's/(.*\/var.*)(,nosuid)(.*)/\1\3/' /etc/fstab
confirm that nosuid is gone on line /var
diff /etc/fstab /etc/fstab.bak
# diff /etc/fstab /etc/fstab.bak
6c6
< 7a165224832557cb.e /var ffs rw,nodev 1 2
---
> 7a165224832557cb.e /var ffs rw,nodev,nosuid 1 2
Name Resolving
as the HTTP Daemon is running in a chrooted environment, we have to provide him the resolv.conf file
mkdir /var/www/etc
cp /etc/resolv.conf /var/www/etc/
finally restart all services
rcctl restart bgpd httpd slowcgi
# rcctl restart bgpd httpd slowcgi
bgpd(ok)
bgpd(ok)
httpd(ok)
httpd(ok)
slowcgi(ok)
slowcgi(ok)
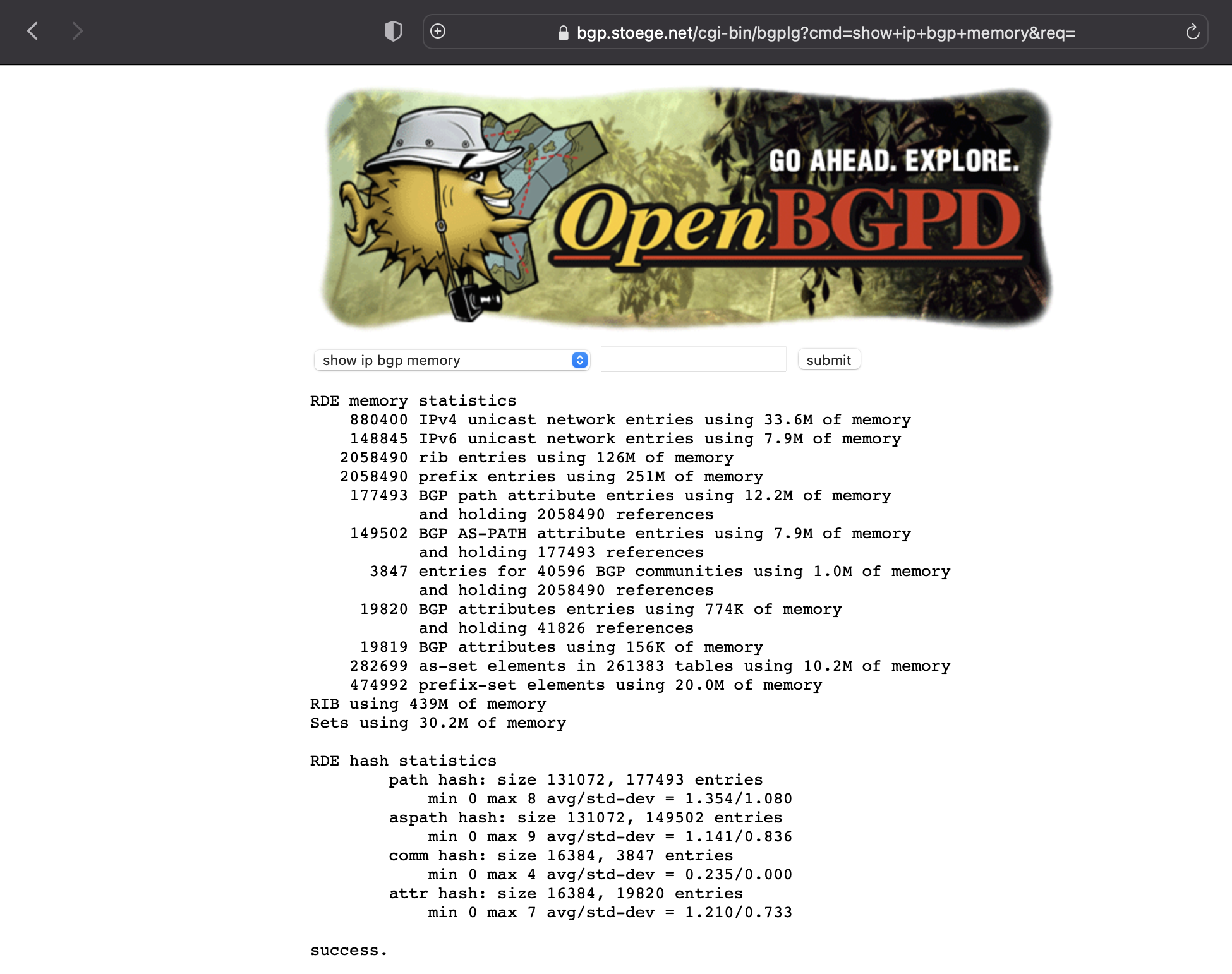
Browse Website
… and here we are … :-)
You can now get the View from the perspective of your Server. Best is you peer with your own BGP Routers the get their view.
Ktrace
ktrace -f bla.out chroot -u www /var/www/ /bin/ping 1.1.1.1
ktrace -f ping.out ping openbsd.org
Any Comments ?
sha256: d2f44969daf78a0b2cc0cd7fb95b2bad125a298d38d1c16c9940eb910b6ee69c